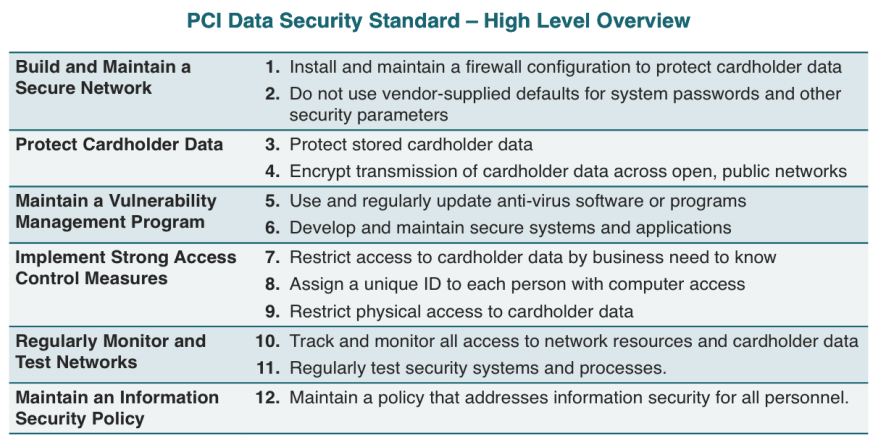
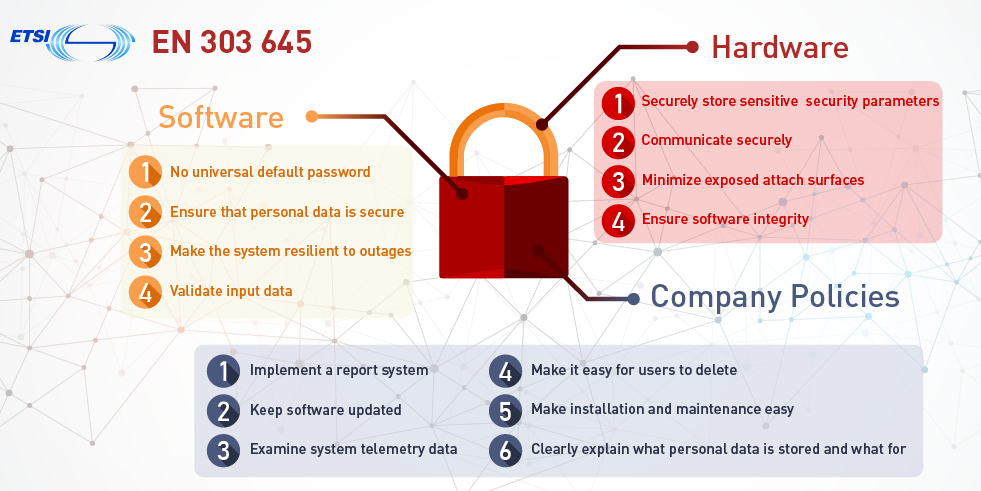
New requirements for the secure design and development of modern payment software - Help Net Security
High Security Standards Concept Icon Stock Illustration - Download Image Now - Abstract, Accessibility, Art - iStock
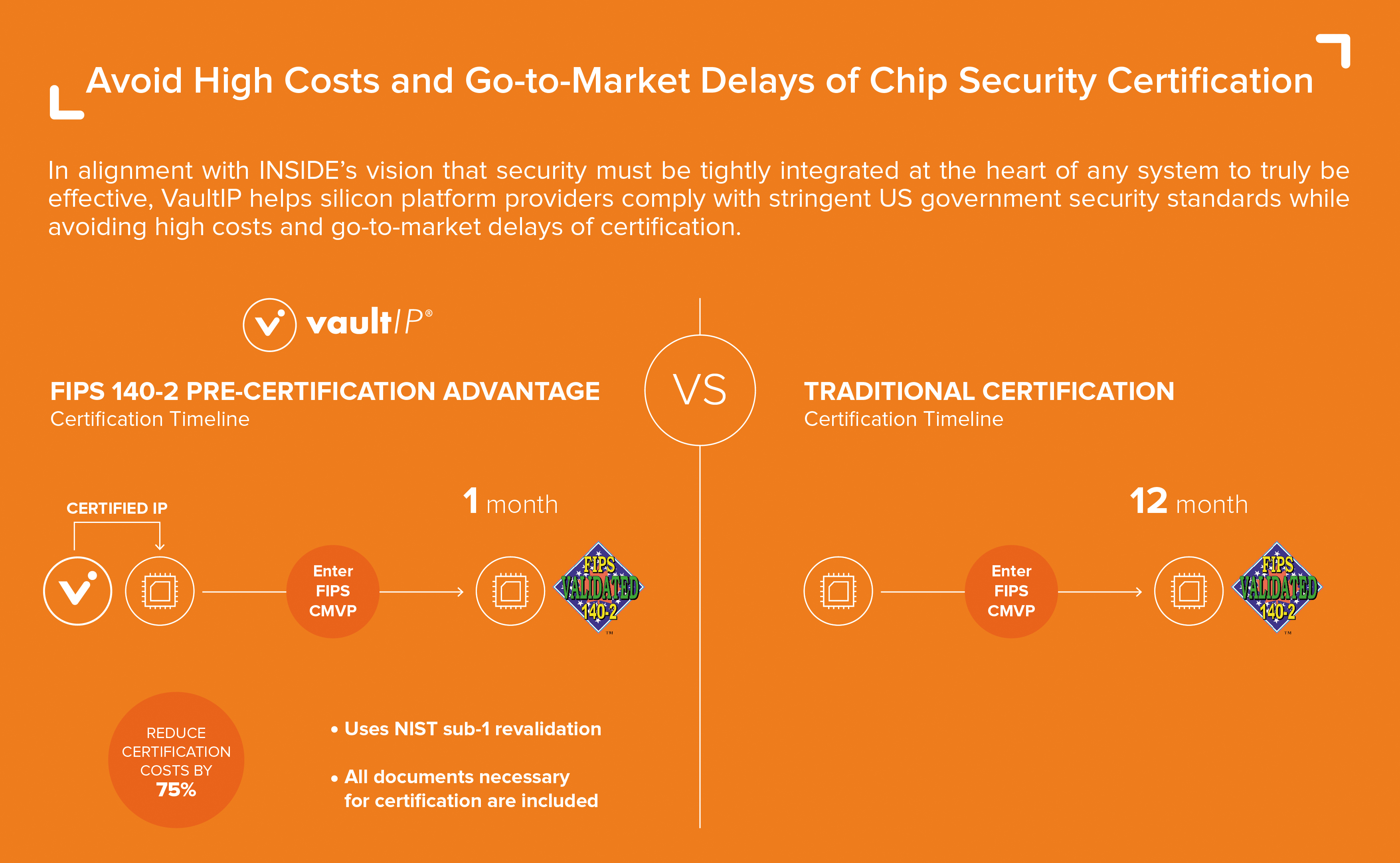
INSIDE Secure Shortens Time to Certification with World's First FIPS 140-2-Certified IP Component | Business Wire